Understanding SHA3_256 Hash for Developers
In the world of cryptography, hash functions play a vital role in securing data. Hash functions are used to transform arbitrary data into fixed-size outputs that are unique to the input data. One such hash function is SHA3_256, which is a member of the SHA-3 family of hash functions.
Concept and How It Works
SHA3_256 is a cryptographic hash function that generates a 256-bit hash value for the input data. It follows the sponge construction, which means that it absorbs the input data and then squeezes out the hash value. The sponge construction is used to improve the security of the hash function by preventing certain types of attacks.
To generate a hash value using SHA3_256, the input data is first padded to ensure that its length is a multiple of 1088 bits. The padded input is then divided into 1088-bit blocks, which are processed one at a time. Each block is absorbed and then squeezed to generate a 256-bit hash value. Finally, all the hash values are concatenated to produce the final hash value.
Sample Code or Commands
The following is an example of how to generate a SHA3_256 hash value in Python:
import hashlib
input_data = b'Example data to be hashed'
hash_object = hashlib.sha3_256(input_data)
hash_value = hash_object.hexdigest()
print(hash_value)Scenarios for Developers
As a developer, you may need to use SHA3_256 hash function in various scenarios such as:
- Password storage and authentication
- Digital signatures
- Key derivation
- Data integrity verification
- Random number generation
Key Features
The key features of SHA3_256 hash function are:
- Generates a fixed-size 256-bit hash value
- Resistant to collision attacks
- Secure against preimage attacks
- Efficient implementation on hardware devices
- Lightweight computation on software platforms
Misconceptions and FAQs
Misconception 1: SHA3_256 is unbreakable
SHA3_256 is a secure hash function, but it is not unbreakable. Like any other cryptographic algorithm, it is subject to attacks, such as brute-force attacks and side-channel attacks. However, the security level of SHA3_256 is high enough to provide reasonable protection against most attacks.
Misconception 2: SHA3_256 is the best hash function
SHA3_256 is a widely used hash function, but it is not necessarily the best one for all applications. The choice of hash function depends on the specific requirements of the application, such as security level, performance, and implementation constraints.
FAQ 1: Can SHA3_256 be used for password storage?
Yes, SHA3_256 can be used for password storage, but it is recommended to use a salted hash function, such as PBKDF2 or bcrypt, to enhance the security of the passwords.
FAQ 2: Can SHA3_256 be used for digital signatures?
Yes, SHA3_256 can be used as a part of digital signature schemes, such as the ECDSA and EdDSA signature schemes.
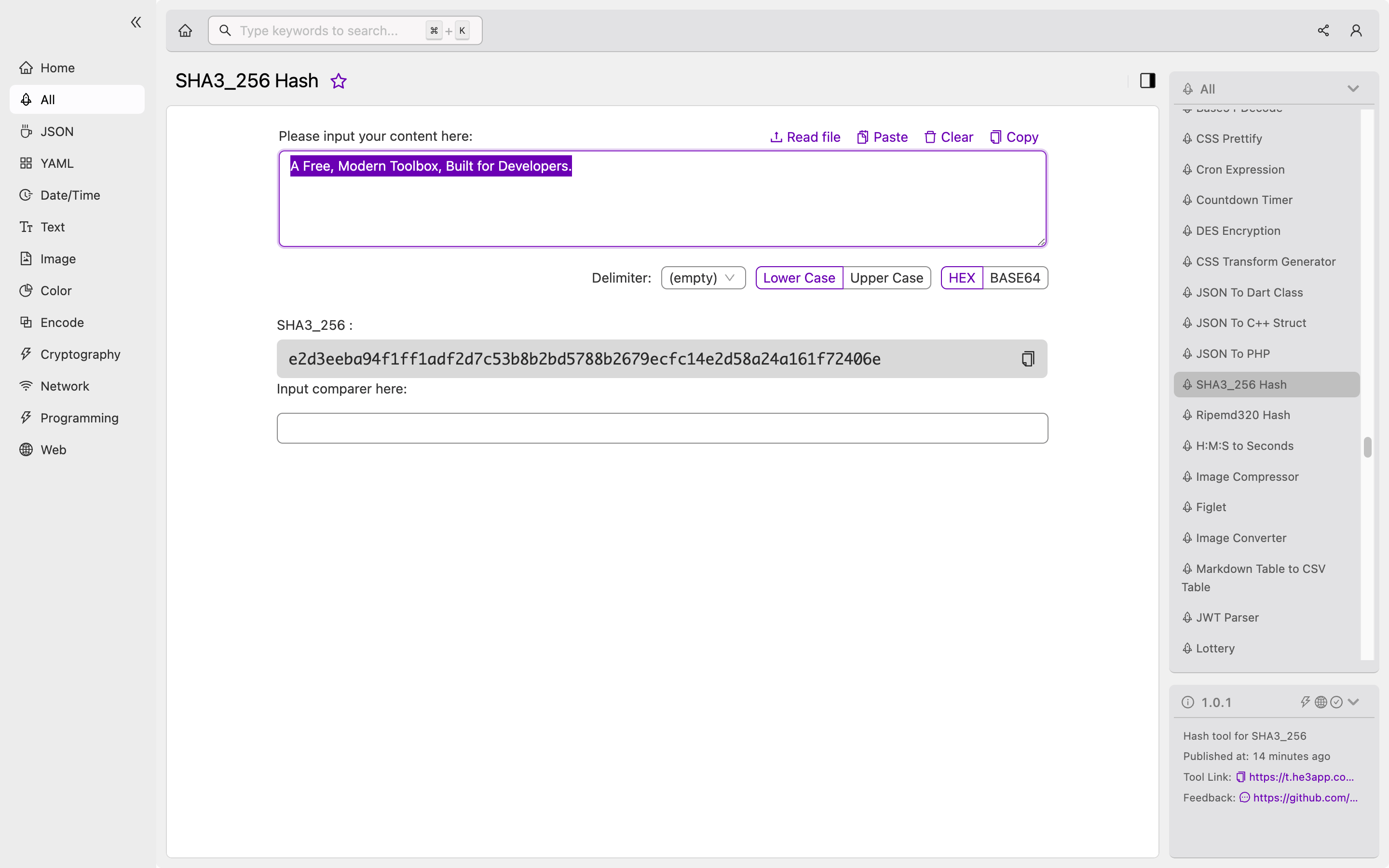
How to Use SHA3_256 Hash Tool
Or you can use SHA3_256 Hash tool in He3 Toolbox (https://t.he3app.com?1ngn) easily.
Conclusion
SHA3_256 is a secure hash function that is widely used in various applications, such as password storage, digital signatures, and data integrity verification. As a developer, it is essential to understand the concept and key features of SHA3_256 to use it effectively and securely. For more information, you can visit the Wikipedia page and the NIST page.
